Security Operations Center (SOC): The Practical Guide for Modern Security Teams

A Security Operations Center (SOC) is supposed to be the nerve center of an organization’s security program. In reality, many SOCs struggle with alert fatigue, tool sprawl, unclear responsibilities, and rising costs while still missing real threats.
This guide is written to fix that.
Whether you are building a SOC from scratch, modernizing an existing one, or deciding whether to outsource to an MSSP, this article explains what a SOC actually does, how it should be designed, and how modern SOCs operate in practice not in theory.
What Is a Security Operations Center (SOC)?
A Security Operations Center (SOC) is a centralized function responsible for monitoring, detecting, investigating, and responding to cybersecurity threats across an organization’s environment.
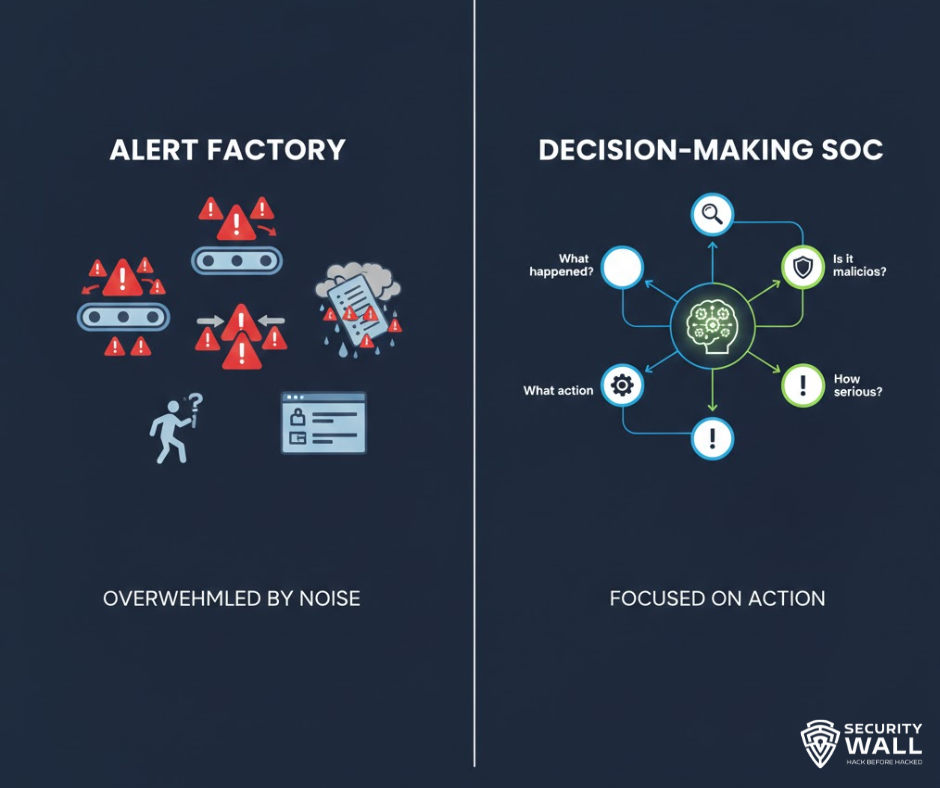
At its core, a SOC answers four questions continuously:
- What is happening in our environment right now?
- Is it malicious or risky?
- How serious is it?
- What action should we take?
A SOC is not:
- Just a SIEM dashboard
- A ticket-closing factory
- A compliance-only logging system
A well-functioning SOC is a decision-making engine, not just an alert-processing unit.
What Does a SOC Monitor?
One of the most common SOC failures is trying to monitor everything. Effective SOCs focus on high-signal telemetry that aligns with real attack paths.
Network and Firewall Activity
- Inbound and outbound connections
- Lateral movement attempts
- Policy violations
- Known malicious IPs and command-and-control patterns
The goal is behavioral visibility, not logging every packet.
Endpoint and EDR Signals
- Process execution
- Privilege escalation
- Suspicious parent-child processes
- Persistence mechanisms
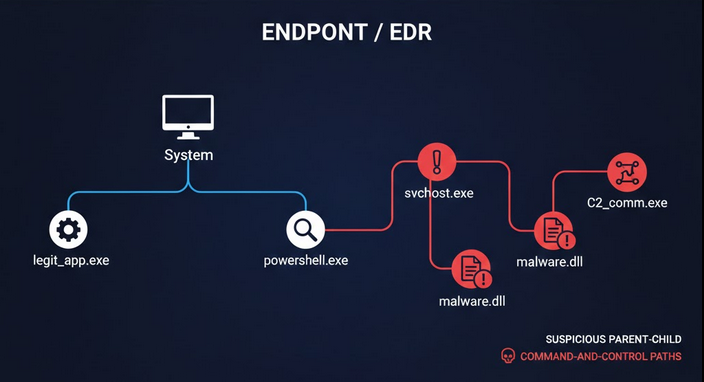
Modern SOCs rely heavily on endpoint telemetry because most attacks eventually touch an endpoint, even in cloud-heavy environments.
Cloud and Identity Activity
- IAM changes
- Privileged role usage
- API calls and automation misuse
- Suspicious authentication behavior
Cloud environments shift the SOC’s focus from perimeter defense to identity and access monitoring.
Web, DNS, and Email Telemetry
- Malicious domain access
- Phishing attempts
- Data exfiltration indicators
- DNS-based command-and-control
These signals often provide early indicators of compromise, before endpoint alerts fire.
SOC Team Structure and Roles
A SOC is not defined by tools it’s defined by people and responsibilities.
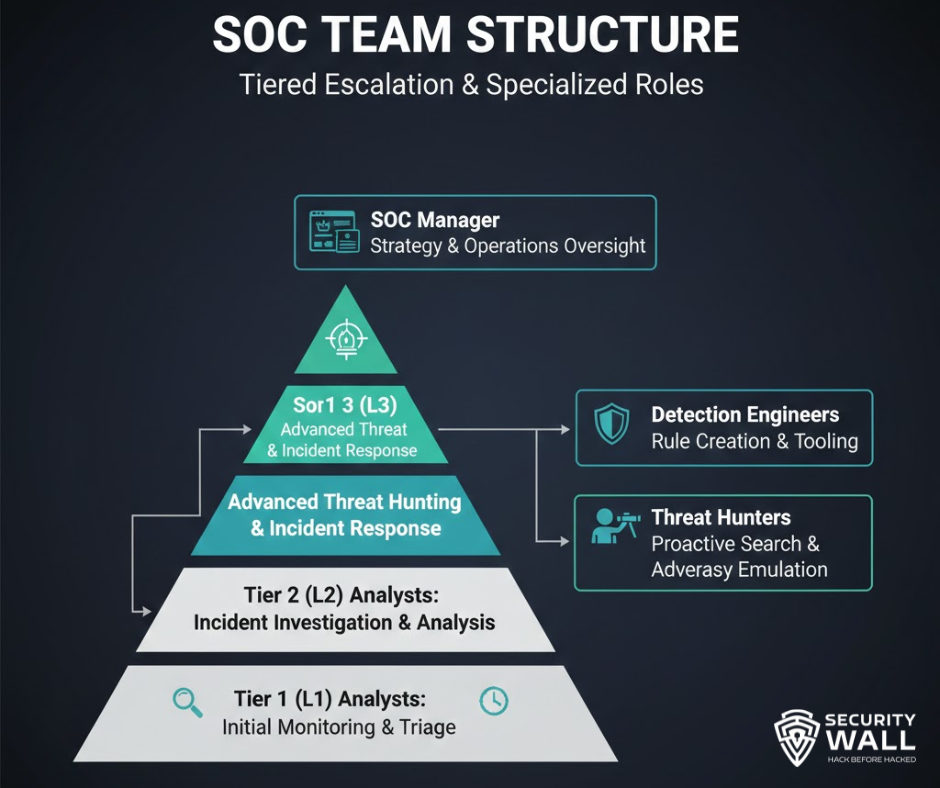
L1 SOC Analysts (Monitoring & Triage)
- Validate alerts
- Perform initial enrichment
- Follow playbooks
- Escalate confirmed incidents
The biggest risk at L1 is burnout, usually caused by noisy alerts and unclear escalation criteria.
L2 Analysts (Investigation & Analysis)
- Deep-dive investigations
- Correlate multiple data sources
- Determine scope and impact
- Recommend containment actions
L2 analysts bridge the gap between alerts and incidents.
L3 Analysts / Incident Responders
- Advanced threat analysis
- Malware analysis
- Complex incident handling
- Root cause analysis
In smaller SOCs, this role may be part-time or outsourced.
Detection Engineers
- Build and maintain detection rules
- Tune alerts
- Reduce false positives
- Map detections to attacker techniques
Without detection engineering ownership, SOCs drown in noise.
Threat Hunters
- Proactively search for hidden threats
- Develop hypotheses based on attacker behavior
- Turn hunt findings into new detections
Threat hunting is a maturity capability, not a starting point.
SOC Manager
- Owns metrics, staffing, and priorities
- Balances detection quality vs analyst workload
- Interfaces with leadership and compliance
SOC Tools Explained (Without Vendor Bias)
Tools enable a SOC, but too many tools cripple it.
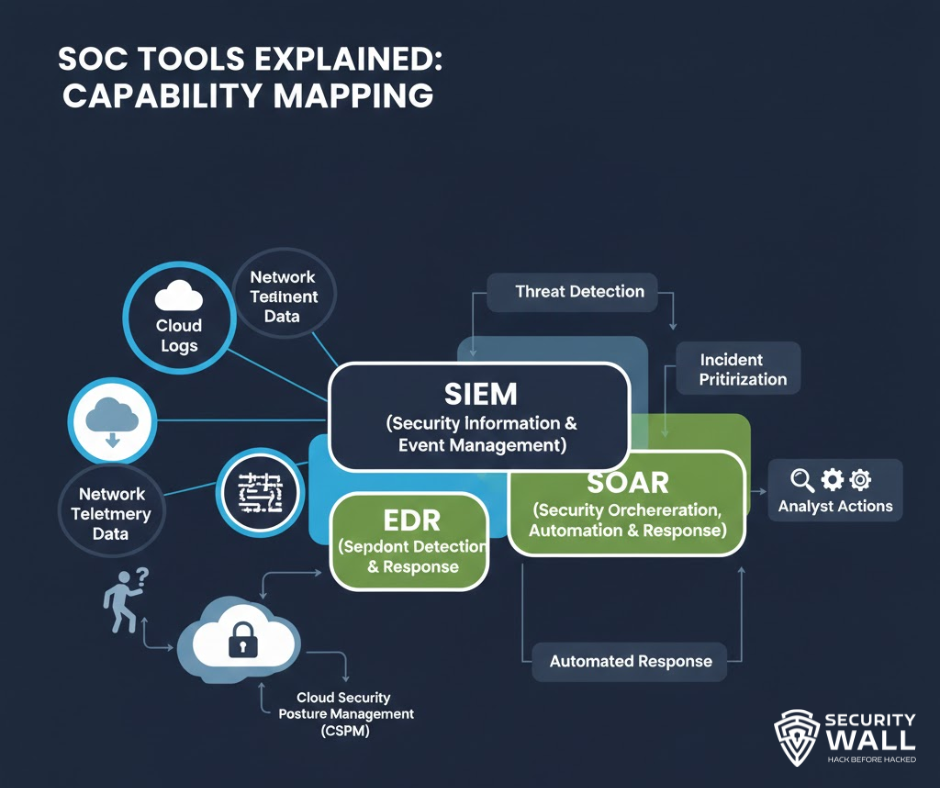
SIEM (Security Information and Event Management)
Strengths
- Centralized visibility
- Correlation across data sources
- Compliance reporting
Limitations
- High ingestion costs
- Noisy detections if poorly tuned
- Slow investigations without enrichment
A SIEM should be a correlation and context engine, not a dumping ground.
EDR (Endpoint Detection and Response)
- High-fidelity endpoint telemetry
- Fast containment capabilities
- Strong behavioral detections
Most modern SOCs treat EDR as a primary detection source, not secondary.
SOAR (Security Orchestration, Automation, and Response)
- Automates repetitive tasks
- Enforces playbooks
- Reduces analyst workload
Automation should start with enrichment and containment, not full auto-response.
Cloud-Native Security Tools
- Cloud provider logging
- Identity protection
- SaaS visibility
These tools are critical as infrastructure moves away from traditional networks.
SOC Architecture: Modern vs Legacy
Legacy SOC Architecture
- Heavy perimeter focus
- Firewall-centric
- Static rules
- Manual workflows
This model struggles in cloud-first and remote-work environments.
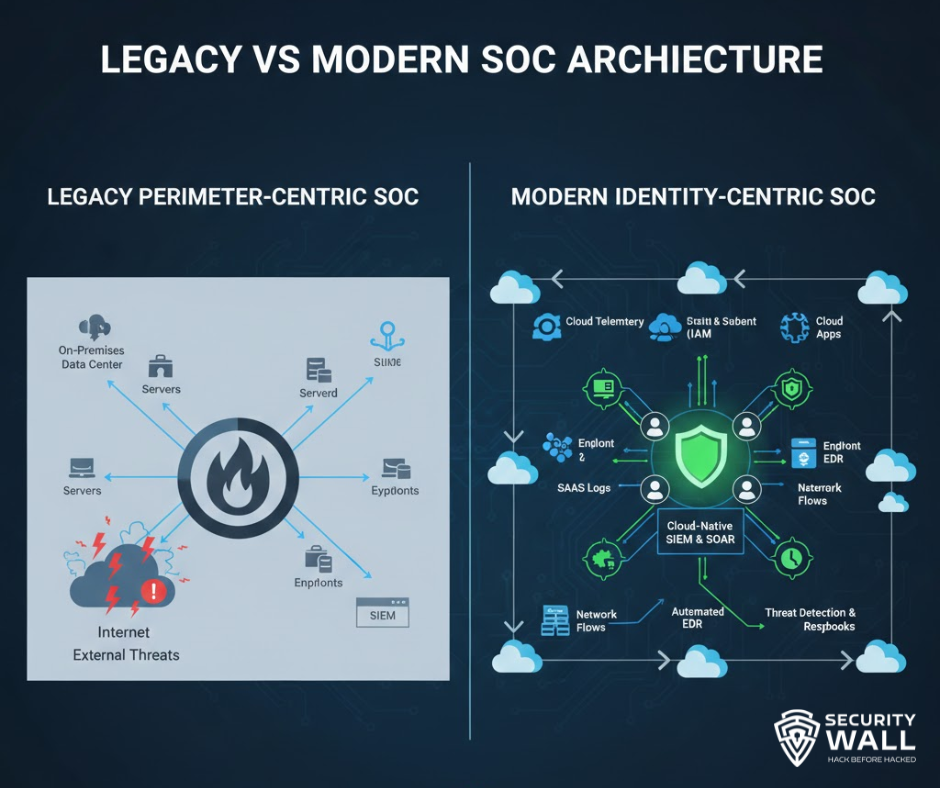
Modern SOC Architecture
- Identity-centric
- Endpoint-driven detections
- Cloud-native telemetry
- Integrated automation
Modern SOCs prioritize context, correlation, and speed over volume.
Build a SOC vs Outsource to an MSSP
This is one of the most searched SOC questions and the answer depends on context.
When Building an In-House SOC Makes Sense
- Large or regulated organizations
- Need for deep business context
- Mature security teams
- 24/7 staffing budget
When an MSSP Is the Better Option
- Small to mid-sized organizations
- Limited internal expertise
- Need for fast coverage
- Budget constraints
Key Tradeoffs
| Factor | In-House SOC | MSSP |
|---|---|---|
| Control | High | Medium |
| Cost | High | Predictable |
| Context | Strong | Varies |
| Scalability | Slow | Fast |
Many organizations adopt a hybrid model: internal SOC ownership with MSSP support.
SOC Automation and Alert Fatigue
Alert fatigue is the #1 reason SOCs fail.
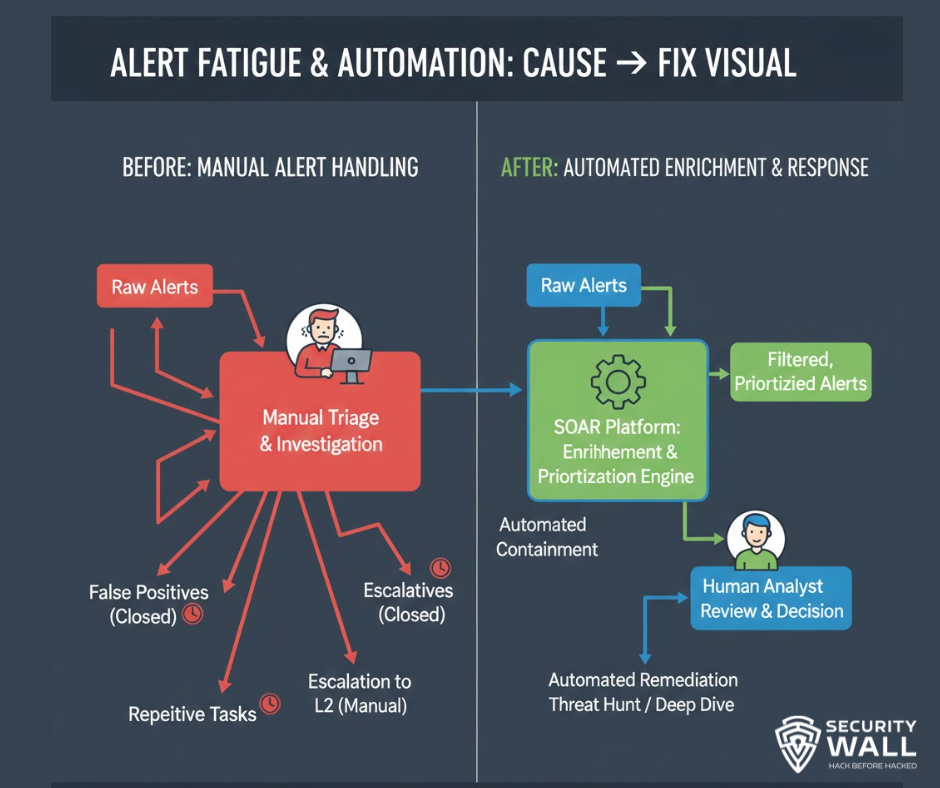
Why SOCs Drown in Alerts
- Poorly written detection rules
- Duplicate alerts from multiple tools
- No suppression or prioritization
- Compliance-driven logging overload
What to Automate First
- Alert enrichment
- Threat intelligence lookups
- Asset context gathering
- Simple containment actions
Automation should remove toil, not replace judgment.
What NOT to Automate
- Complex incident decisions
- High-risk containment without context
- Business-impacting actions
Compliance and SOC Monitoring
Compliance often drives SOC creation but it shouldn’t define SOC quality.
Common Frameworks
- SOC 1 / SOC 2
- ISO 27001
- PCI DSS
What Auditors Actually Expect
- Log retention
- Access monitoring
- Incident response evidence
- Alert handling processes
A compliant SOC can still be ineffective if detections lack quality.
SOC Maturity Model
Most SOCs evolve through predictable stages:
Level 1: Reactive Monitoring
- Basic alerting
- Manual response
- High noise
Level 2: Alert-Driven SOC
- SIEM-based workflows
- Defined escalation paths
- Limited automation
Level 3: Context-Aware SOC
- Integrated tools
- Enrichment and prioritization
- Reduced false positives
Level 4: Threat-Informed SOC
- MITRE ATT&CK-aligned detections
- Regular threat hunting
- Continuous improvement
Level 5: Optimized SOC
- Metrics-driven
- Business-context detections
- Proactive risk reduction
Common SOC Problems (Real-World)
If your SOC struggles, it’s usually due to:
- Too many alerts, too little context
- SIEM cost overruns
- Poor cloud visibility
- Analyst burnout
- No detection ownership
Fixing these requires process and prioritization, not more tools.
A Security Operations Center is not a product you buy it’s a capability you build over time.
The most successful Security Operation Center:
- Focus on signal over noise
- Invest in detection quality
- Protect analyst time
- Evolve with the threat landscape
Whether you’re starting small or scaling globally, the goal remains the same
detect real threats early and respond effectively.




