SAMA Penetration Testing: Common Mistakes by Banks

SAMA penetration testing is often misunderstood as a technical checkbox rather than a regulatory assurance mechanism. Many banks and financing companies in Saudi Arabia perform penetration testing or VAPT regularly, yet still face challenges during SAMA audits.
The issue is rarely the absence of testing. It is the misalignment between how testing is performed and how SAMA evaluates evidence.
Organizations that treat penetration testing as a compliance enabler not just a technical task experience smoother audits, faster closure of findings, and greater supervisory confidence. This is the approach SecurityWall has consistently applied while supporting SAMA-regulated entities across Saudi Arabia for numerous client.
1. What SAMA Expects From Penetration Testing
SAMA does not mandate a specific penetration testing framework, tool, or vendor. This flexibility is intentional, but it also creates risk when organizations interpret it too loosely.
In practice, SAMA expects penetration testing to serve as evidence of control effectiveness, not just evidence of activity.
During supervisory reviews, the focus is often on:
- Whether testing covers systems that support regulated services
- Whether realistic attack paths are evaluated
- Whether findings are actionable and tracked through remediation
- Whether results feed back into governance and risk decisions
Penetration testing programs designed with these outcomes in mind such as SecurityWall’s structured penetration testing produce evidence that stands up far more effectively during regulatory discussions.
This is also why penetration testing is most effective when embedded within a broader SAMA cybersecurity compliance program, rather than treated as an isolated technical activity.
Penetration testing is most effective when it is treated as part of a broader SAMA compliance strategy, rather than a standalone technical activity. This approach is explored in more detail in our guide on SAMA cybersecurity compliance in Saudi Arabia.
| What Banks Assume Is Enough | What SAMA Actually Evaluates |
|---|---|
| Annual penetration test completed | Relevance of testing to regulated services |
| Tool-based VAPT report | Evidence of realistic attack simulation |
| Vulnerabilities identified | Exploitation paths and business impact |
| Issues fixed once | Retesting and proof of remediation |
| Clean audit history | Continuous validation and improvement |
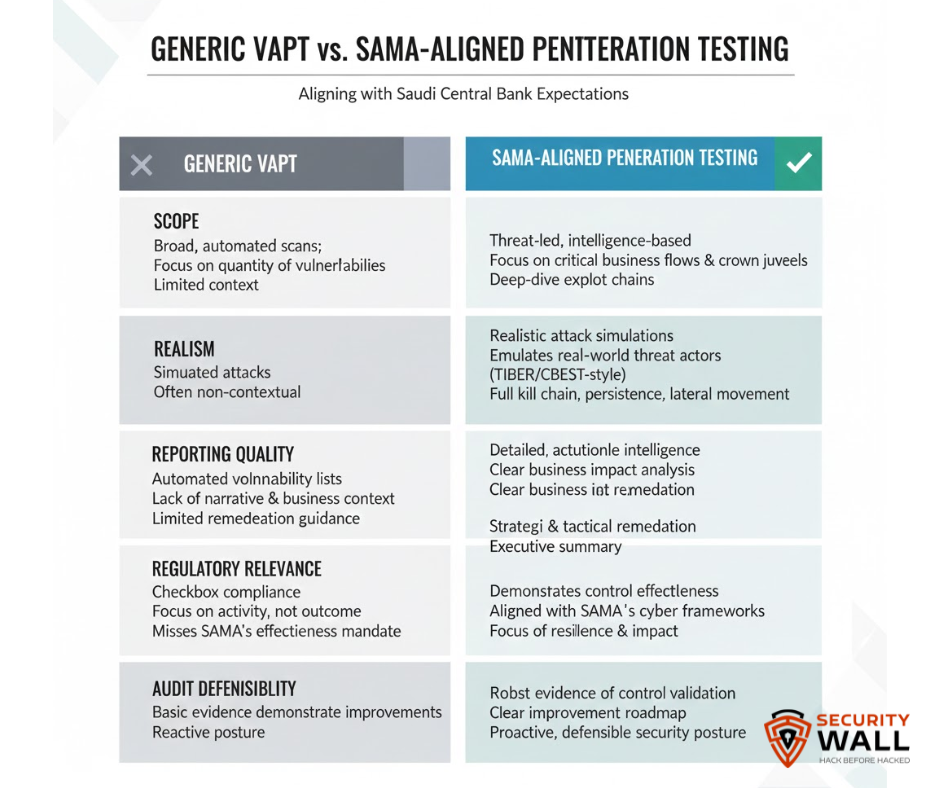
2. Why Generic VAPT Fails SAMA Expectations
Many financial institutions rely on generic VAPT models that were never designed for regulatory scrutiny. These approaches are typically:
- Tool-driven rather than risk-driven
- Broad but shallow in coverage
- Disconnected from business impact
- Difficult to map to SAMA control domains
While generic VAPT can identify vulnerabilities, it often fails to answer the questions regulators actually care about:
- Can this weakness be exploited in your environment?
- What is the impact on regulated services?
- How do you know the control is now effective?
This is why SAMA-aligned VAPT increasingly incorporates assumed-breach logic, where testing starts from the perspective that perimeter controls may already be bypassed. Techniques such as assumed breach testing help validate internal controls, lateral movement resistance, and detection capabilities areas that traditional VAPT often ignores.
3. Common Scope and Methodology Mistakes in SAMA Penetration Testing
Across Saudi banks, financing companies, and fintech platforms, several recurring issues appear during audits.
3.1 Testing the Wrong Assets
Testing often excludes:
- Mobile applications supporting financial transactions
- APIs and integration layers
- Cloud-hosted components
- Third-party access paths
Given the rise of digital channels, omitting areas such as mobile applications which can be addressed through targeted mobile application penetration testing often raises immediate concerns.
3.2 Treating Scope as a Checklist
Overly broad scopes lead to:
- Superficial findings
- Low remediation value
- Weak audit narratives
SAMA reviewers generally prefer focused, high-quality testing over large volumes of low-impact results.
3.3 Reporting That Is Technically Correct but Regulator-Unfriendly
Reports that lack:
- Clear linkage to SAMA controls
- Risk-based prioritization
- Management-level summaries
tend to create follow-up questions rather than confidence.
4. How Proper SAMA-Aligned Penetration Testing Reduces Audit Friction
When penetration testing is designed with regulatory outcomes in mind, the audit experience changes noticeably.
SAMA-aligned testing allows institutions to:
- Justify scope decisions clearly
- Demonstrate control effectiveness with evidence
- Show remediation progress over time
- Maintain consistency across audit cycles
Instead of reacting to audit findings, organizations are able to proactively explain their security posture.
This is also where integrating penetration testing into a broader assurance model including more advanced exercises such as red teaming becomes valuable. Ethical red team engagements help validate not just prevention, but detection and response, which are increasingly relevant in mature SAMA reviews.
Many institutions also rely on SLASH to operationalize their compliance programs, ensuring that penetration testing, assumed-breach exercises, and red team outcomes are consistently documented and defensible during regulatory discussions.
Talk to a SAMA compliance expert before audit gaps turn into regulatory findings
5. Why Experienced Vendors Make a Measurable Difference
SAMA penetration testing is as much about regulatory context as it is about technical skill.
Vendors without Saudi regulatory experience often deliver:
- Generic methodologies
- Globally formatted reports
- Limited audit defensibility
By contrast, vendors who have worked extensively with SAMA-regulated entities understand:
- How SAMA interprets testing evidence
- What audit teams probe during discussions
- How to structure findings for compliance consumption
- When escalation from VAPT to red team exercises is appropriate
This experience translates directly into fewer audit surprises, faster closure of observations, and stronger supervisory confidence.
Organizations looking to understand how penetration testing fits into the broader SAMA compliance journey can also refer to detailed guide on SAMA cybersecurity compliance in Saudi Arabia which ties testing, governance, and regulatory expectations together.
SAMA penetration testing is not about running tools or producing reports. It is about demonstrating that security controls work under real conditions.
Financial institutions that rely on generic VAPT approaches often discover gaps during audits when remediation timelines are tight and regulatory pressure is high. Institutions that adopt SAMA-aligned penetration testing strategies discover those gaps earlier and fix them on their own terms.
The difference is not effort. It is alignment.




