SAMA Cybersecurity Compliance in Saudi Arabia: Testing vs Documentation

For most SAMA-regulated organizations in Saudi Arabia, cybersecurity compliance no longer fails because of missing policies. Over the last few years, banks, fintechs, financing companies, and payment platforms have invested heavily in documentation, governance frameworks, and compliance tooling.
Policies exist. Control matrices are mapped. Evidence repositories are maintained. Audit readiness has improved significantly across the sector.
And yet, cybersecurity incidents, audit observations, and regulatory escalations continue to occur often inside organizations that are technically “compliant.”
This contradiction is not accidental. It exists because compliance documentation and control effectiveness are not the same thing, even though they are often treated as if they were.
Saudi Cybersecurity Market Context (Economic Signals of Rising Risk)
| Metric | Value | Source |
|---|---|---|
| Cybersecurity Spend (2024) | ~15.2 B SAR (~4 B USD) | National Cybersecurity Authority |
| Cybersecurity Workforce (2024) | > 21,000 professionals | National Cybersecurity Authority |
| Attack Increase (2024) | +35% year-on-year | MarkNtel Advisors |
| Business Impacting Attacks | > 95% organizations affected | Security Middle East Magazine |
| Identity Attack Prevalence | > 97% of malicious login events | Microsoft Security Research |
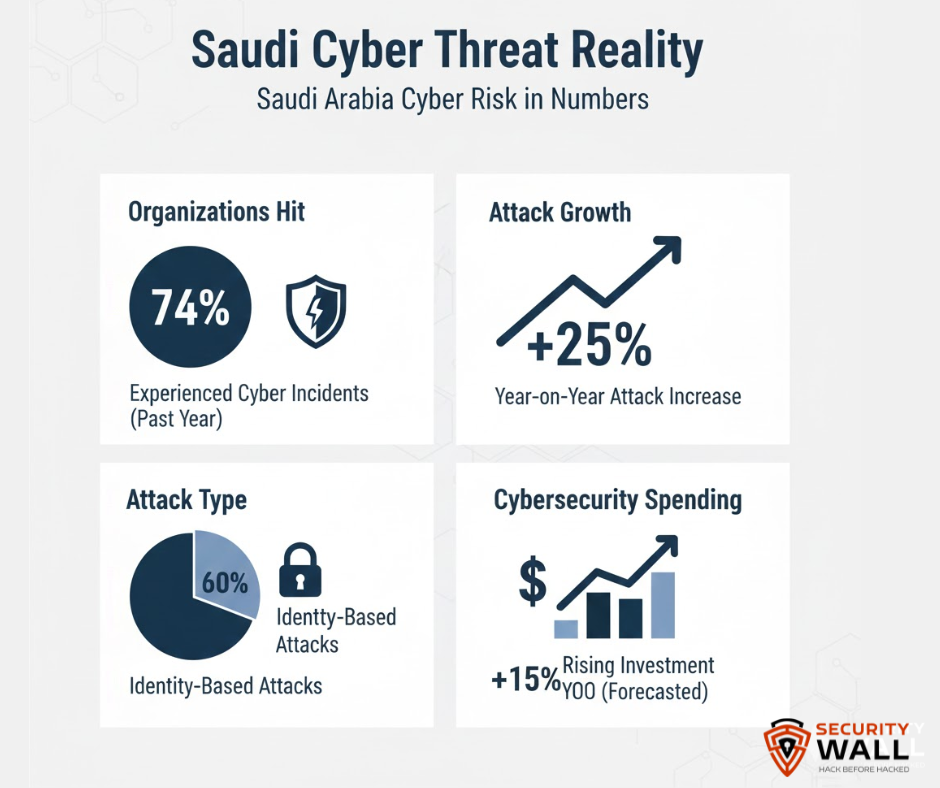
These figures show a dual dynamic investments are increasing, but threats are scaling faster. That’s exactly why compliance documentation is no longer sufficient it must be backed by rigorous validation and real-world testing.
In this environment, regulators (including SAMA) are not just asking whether you have policies. They are increasingly scrutinising whether those policies translate into controls that work against the threats organizations actually encounter.
Where Most SAMA Compliance Programs Quietly Break Down
In theory, SAMA compliance follows a logical lifecycle: define controls, implement them, monitor them, and improve them. In practice, most organizations slow down or stop after the first two steps.
Documentation gives a sense of closure. Testing does not.
What we repeatedly see in SAMA-regulated environments is that compliance programs are optimized to pass reviews, not to withstand pressure. This creates a blind spot that only becomes visible when someone actively challenges the environment.
That challenge does not usually come from internal reviews. It comes from:
- Supervisory questioning
- External testing mandates
- Or real-world incidents
By that point, the organization is no longer learning proactively it is reacting.
Why Documentation Alone Is Not Enough (And Never Was)
SAMA frameworks are intentionally principle-based. They are meant to scale across banks, insurers, fintechs, BNPL platforms, and other financial entities with very different risk profiles.
But principle-based frameworks also rely heavily on organizational interpretation.
When compliance is driven primarily by documentation, several predictable patterns emerge:
- Controls are designed to satisfy framework wording, not attacker behavior
- Effectiveness is assumed based on design, not validated through execution
- Dependencies between systems, people, and vendors are not stress-tested
On paper, controls appear complete.
Operationally, many of them have never been exercised under realistic conditions.
This is not a failure of intent. It is a failure of validation.
| Interaction Length | Consistent Refusal Rate | Partial Compliance Observed |
|---|---|---|
| 1 turn | High | Rare |
| 3–5 turns | Medium | Occasional |
| 6+ turns | Low | Common |
What SAMA Really Means by “Effective Cybersecurity Controls”
In SAMA supervisory discussions, the conversation increasingly shifts away from existence and toward evidence.
The implicit question behind many regulatory interactions is simple:
How do you know this control works not in theory, but in practice?
That question cannot be answered with policies alone.
It is answered through structured cybersecurity testing that aligns with SAMA’s risk domains, threat landscape, and reporting expectations. This is why activities such as SAMA penetration testing, SAMA VAPT, and eventually SAMA Ethical Red Teaming have moved from being technical exercises to becoming core compliance mechanisms.
Organizations that perform SAMA-aligned testing through services such as penetration testing and vulnerability assessment.
are not merely identifying vulnerabilities they are producing regulator-defensible evidence.
Why “We’ll Catch It During the Audit” Is a Dangerous Assumption
Many organizations still rely on audits as their primary safety net. This is a misunderstanding of what audits are designed to do.
Audits assess alignment. They do not simulate attack behavior.
Incidents, on the other hand, are already failures.
By the time a weakness is discovered in either scenario, the organization is already exposed technically, operationally, and reputationally.
Testing changes this equation by shifting discovery left.
It allows organizations to:
- Identify weaknesses before regulators or attackers do
- Remediate issues without time pressure
- Demonstrate continuous improvement across review cycles
This shift from reactive discovery to proactive validation is one of the clearest indicators of cybersecurity maturity in SAMA-regulated environments.
Why Regulators Often Trust Tested Environments More Than “Perfect” Ones
Counter-intuitively, environments with zero findings often trigger more scrutiny, not less.
Experienced supervisors understand that complex financial systems always have weaknesses. What matters is whether those weaknesses are understood, documented, and managed.
The table below reflects how different postures are typically perceived:
| Compliance Posture | Regulatory Confidence |
|---|---|
| Perfect documentation, no testing | Low |
| Some findings, no remediation | Low |
| Findings with clear remediation | Moderate |
| Continuous testing with improvement cycles | High |
Organizations that present structured results from penetration testing, VAPT, or controlled adversarial exercises demonstrate something far more important than technical strength:
They understand their risk.
This understanding builds supervisory confidence far more effectively than flawless documentation ever could.
Where Red Teaming Fits Into SAMA Compliance (And Why It’s Not “Extra”)
As organizations mature, traditional testing reaches its limits. Vulnerabilities may be reduced, but uncertainty remains around detection, response, and decision-making.
This is where SAMA Ethical Red Teaming becomes relevant not as a replacement for compliance, but as its evolution.
Red Teaming tests:
- Whether attacks are detected
- How teams respond under pressure
- Whether escalation and decision paths work in reality
When delivered correctly through services such as red teaming it provides insight into parts of cybersecurity that documentation and standard testing cannot reach.
For SAMA-regulated entities, this is often the difference between appearing compliant and demonstrating resilience.
How Mature Saudi Organizations Actually Structure SAMA Compliance
Organizations that consistently perform well during SAMA supervision tend to follow a layered approach:
- Documentation establishes governance and intent
- Penetration testing and VAPT validate technical controls
- Red Teaming tests organizational response and resilience
- Reporting aligns findings with SAMA language and expectations
- Governance forums treat findings as inputs, not failures
This approach shortens audit cycles, reduces regulatory friction, and builds internal confidence at senior management and board levels.
Vendor experience in Saudi Arabia matters here. Understanding the framework is baseline knowledge. Understanding how SAMA evaluates evidence and follows up is what materially changes outcomes.
SAMA Cybersecurity Compliance in 2026
SAMA cybersecurity compliance has matured and so have expectations.
Today, compliance is not proven by the number of policies in place, but by the organization’s ability to demonstrate that controls work, weaknesses are known, and risks are actively managed.
Testing is no longer optional. It is part of how compliance is demonstrated.
Organizations that accept this early move faster, remediate smarter, and maintain control over regulatory narratives.
Those that don’t usually reach the same conclusion later under far less favorable conditions.




