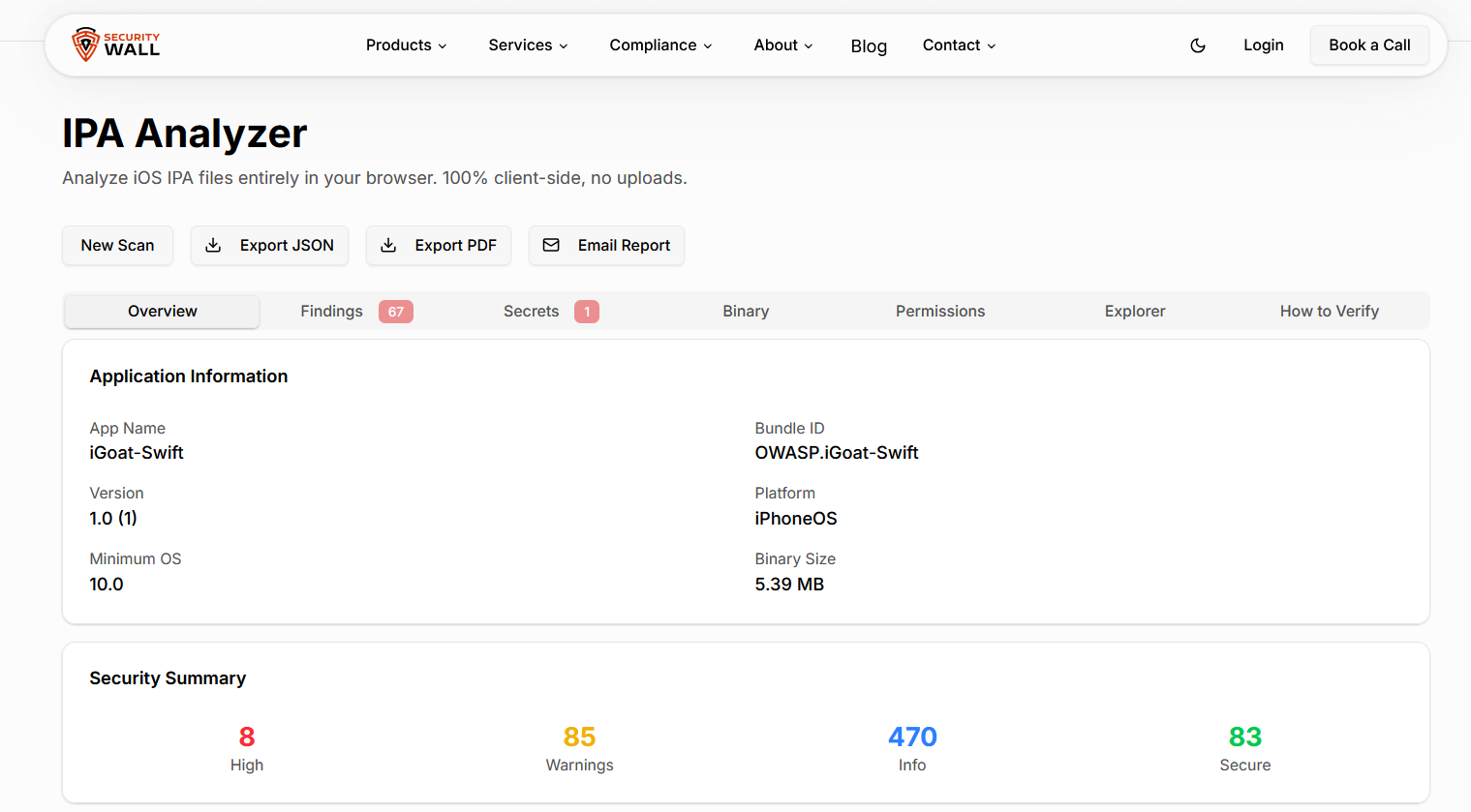
IPA Vulnerability Assessment - Alternative to Manual iOS Security Testing

As iOS applications become more complex and release cycles shorten, traditional approaches to iOS security testing are struggling to keep up. Many security teams still rely heavily on manual reverse engineering and runtime testing to identify vulnerabilities in iOS applications. While these techniques are powerful, they are also time-consuming, inconsistent, and difficult to scale across frequent releases.
This is where IPA vulnerability assessment plays a critical role. By analyzing the IPA file the final packaged form of an iOS application security teams can identify a large class of security issues early, deterministically, and without the overhead of full reverse engineering.
This guide explains what IPA vulnerability assessment is, how it aligns with OWASP MASVS, and why using an automated IPA Security Analyzer is often a faster and more effective alternative to manual iOS security testing.
Why Manual iOS Security Testing Is No Longer Enough
Manual iOS security testing typically involves unpacking the IPA, inspecting binaries, attaching debuggers, intercepting traffic, and analyzing runtime behavior. This approach is valuable, especially for identifying logic flaws and runtime vulnerabilities, but it has practical limitations.
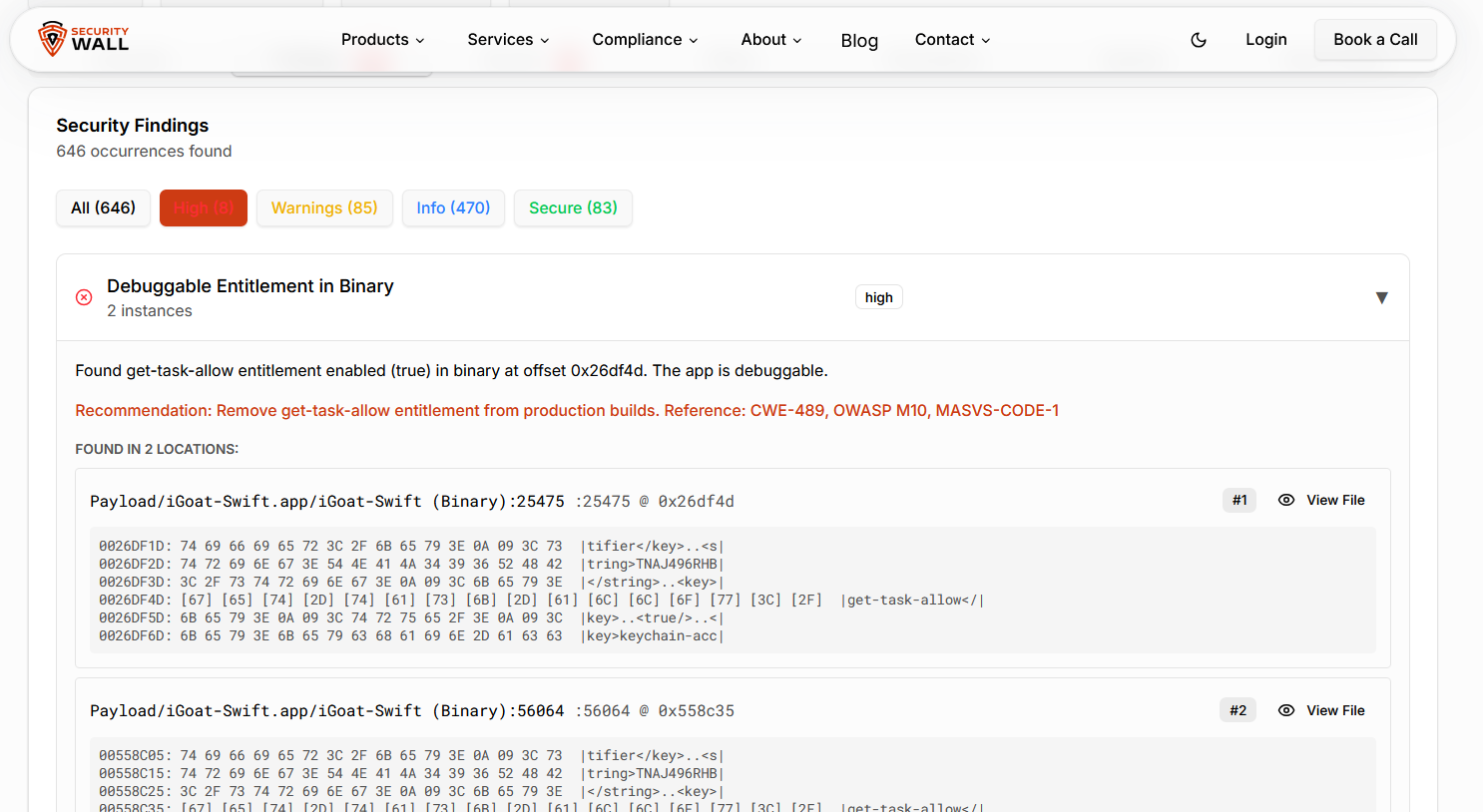
In real-world engagements, a significant amount of time is spent verifying baseline security assumptions before any meaningful findings emerge. Each new build often requires repeating the same steps, even when changes are minimal. As development velocity increases, this creates friction between security teams and engineering teams.
More importantly, many critical iOS vulnerabilities are not logic flaws. They originate from build-time misconfigurations, insecure entitlements, weak binary protections, or secrets embedded during CI/CD processes. These issues are often invisible during runtime testing and surface only after an application is packaged.
Manual testing alone makes it easy for such issues to slip into production unnoticed.
| Aspect | Manual iOS Security Testing | Automated IPA Vulnerability Assessment |
|---|---|---|
| Primary focus | Runtime behavior and application logic | Build-time and configuration security |
| Testing depth | Deep, case-specific analysis | Broad baseline coverage |
| Skill dependency | High — requires senior AppSec expertise | Moderate — rule-driven inspection |
| Repeatability | Low — analyst dependent | High — deterministic checks |
| CI/CD compatibility | Limited | Native |
| Regression detection | Manual comparison between builds | Automatic detection |
| Time per build | High & variable | Low & predictable |
| Best suited for | Logic flaws, abuse cases, advanced threats | MASVS baseline enforcement |
| Failure mode | Missed basics due to fatigue | Limited depth on logic flaws |
Understanding the IPA File from an Attacker’s Perspective
From an attacker’s point of view, the IPA file is a high-value artifact. It contains everything needed to understand how an application behaves in production: configuration, capabilities, binary protections, and embedded resources.
Unlike source code, the IPA reflects the final state of the application after compilation and packaging. Unlike runtime memory, it does not require exploitation to analyze. Any misconfiguration present in the IPA will be faithfully enforced by the operating system.
This is why many OWASP MASVS controls can be validated directly at the IPA level. Platform interaction, transport security, data handling, and exploit resistance are all heavily influenced by build-time decisions that are visible without executing the app.
What IPA Vulnerability Assessment Covers (Mapped to OWASP MASVS)
IPA vulnerability assessment is a static, artifact-based security review focused on identifying build and configuration weaknesses that map directly to OWASP MASVS controls.
| MASVS Domain | Control Focus | What Is Validated | IPA-Level Indicator | Security Risk |
|---|---|---|---|---|
| MASVS-PLATFORM | Least privilege | Application capability scope | Over-privileged entitlements | Expanded attack surface |
| MASVS-PLATFORM | Inter-app communication | URL handling safety | Custom URL schemes | Scheme hijacking |
| MASVS-NETWORK | Secure transport | TLS enforcement | ATS configuration | MITM exposure |
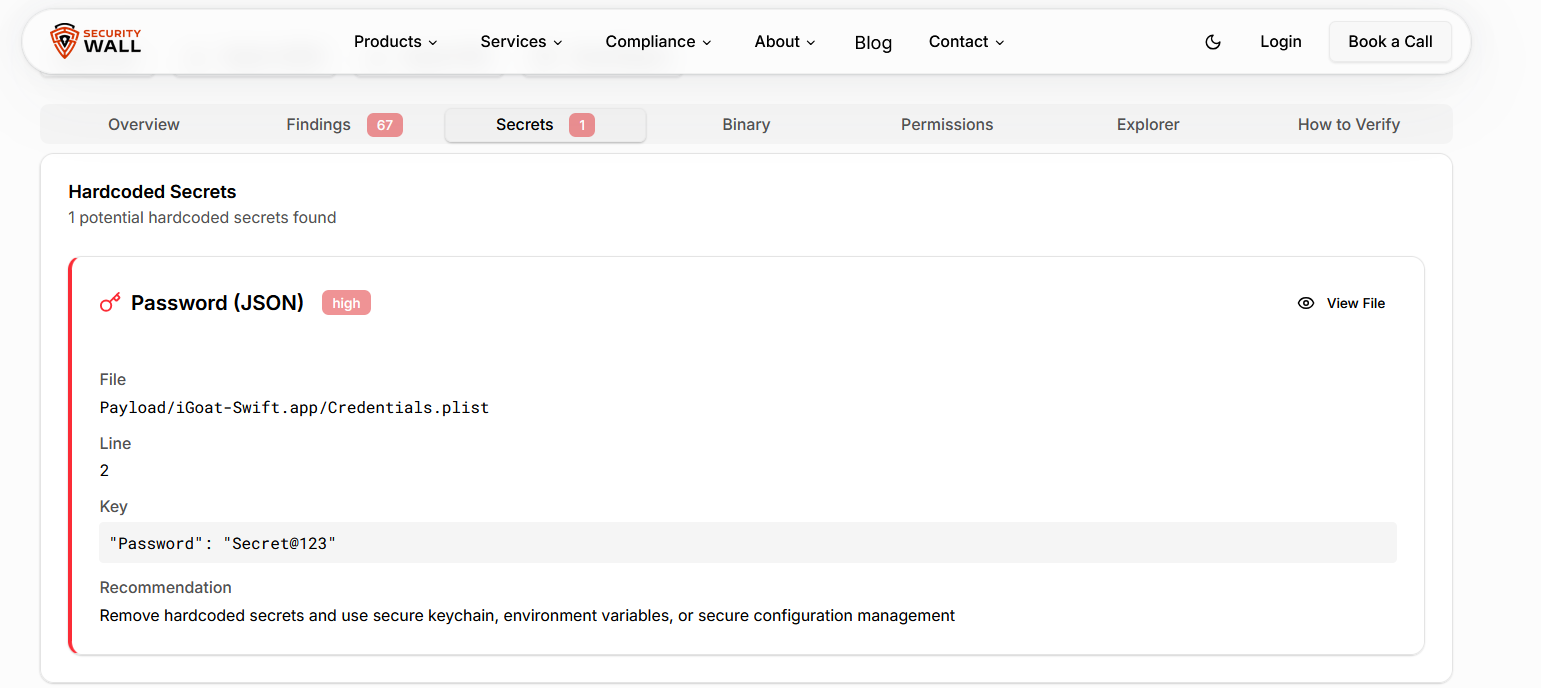
| MASVS-STORAGE | Sensitive data handling | Embedded secrets | API keys, tokens | Backend abuse |
| MASVS-CRYPTO | Crypto baseline | Protection assumptions | Weak or missing indicators | Weak data protection |
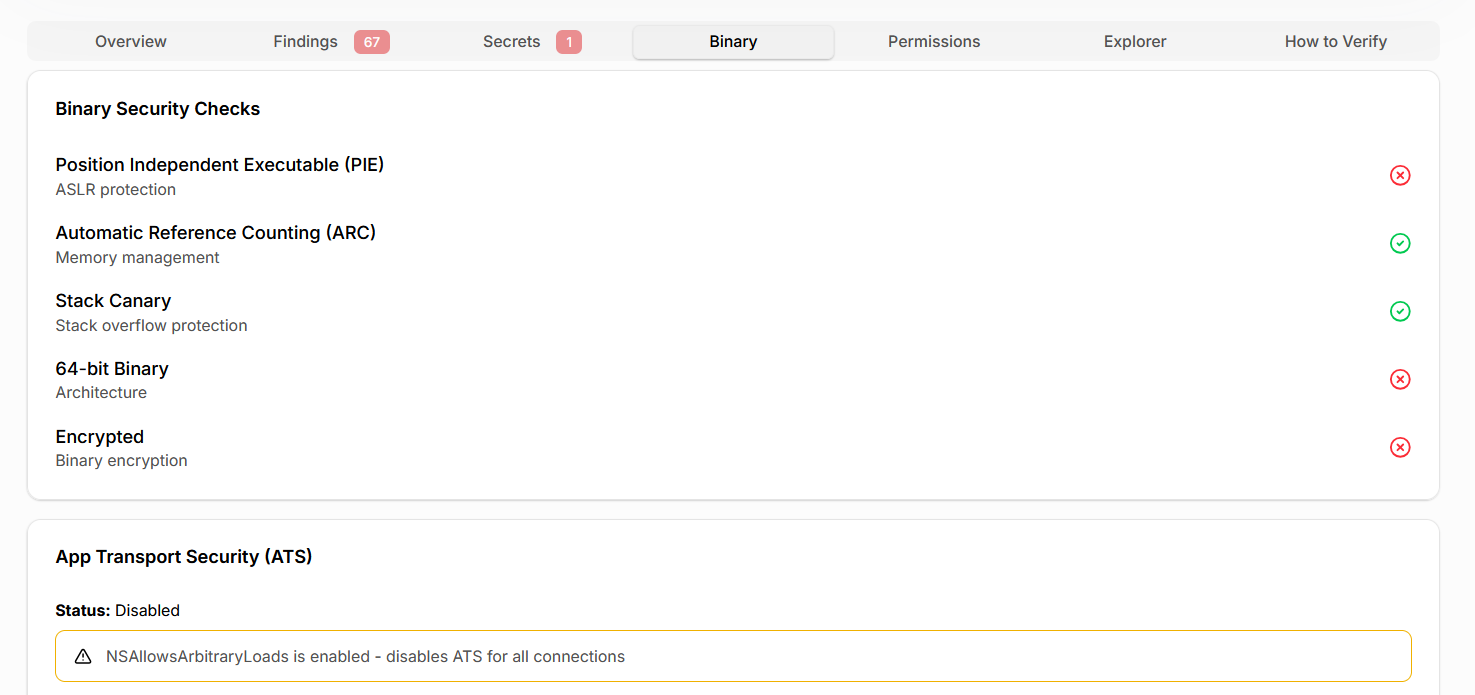
| MASVS-RESILIENCE | Exploit resistance | Binary hardening | Missing PIE, stack canaries | Lower exploit cost |
At the platform level, assessment focuses on application metadata such as Info.plist values, background execution modes, URL schemes, and permission declarations. These elements define how the application interacts with the iOS operating system and are directly related to MASVS-PLATFORM requirements.
Network security controls are evaluated by inspecting App Transport Security configuration. Weak or disabled ATS settings immediately violate MASVS-NETWORK expectations and expose applications to traffic interception risks.
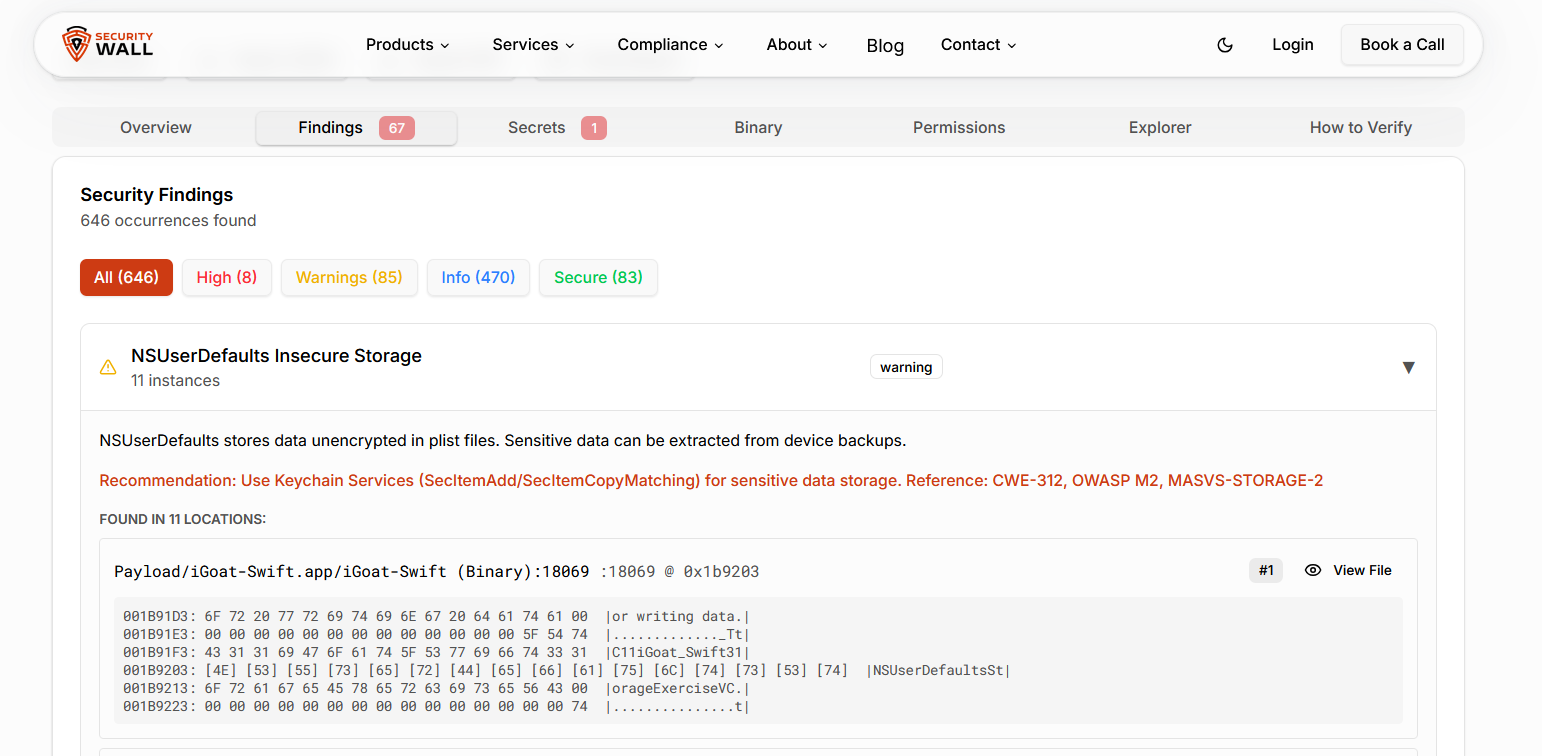
Sensitive data handling is another critical area. API keys, tokens, environment variables, and debug configurations are frequently embedded during the build process. These issues fall under MASVS-STORAGE and MASVS-CRYPTO and are among the most common findings in production IPAs.
Binary hardening is assessed by inspecting Mach-O security flags and encryption settings. Missing exploit mitigations increase the likelihood of successful attacks and directly impact MASVS-RESILIENCE compliance.
An automated IPA Security Analyzer streamlines this process by performing consistent, MASVS-aligned checks across every build, ensuring that security baselines are not silently weakened over time.
Manual IPA Testing vs Automated IPA Vulnerability Assessment
Manual reverse engineering provides depth, but it does not scale well for baseline security validation. IPA vulnerability assessment focuses on coverage and consistency rather than exhaustive runtime analysis.
Manual workflows depend heavily on individual expertise and available time. Important checks are sometimes skipped simply because they are repetitive. Automated assessment removes that variability and allows teams to validate security posture early in the release cycle.
This does not mean that manual testing is obsolete. Instead, IPA assessment acts as a filter. It identifies configuration and build-time issues early, allowing security teams to reserve manual testing for areas where runtime behavior and business logic truly matter.
In practice, many organizations combine IPA vulnerability assessment with professional mobile application penetration testing to achieve both breadth and depth in their security programs.
How IPA Vulnerability Assessment Fits into a Modern AppSec Program
A practical iOS AppSec workflow treats IPA vulnerability assessment as a pre-release security gate. Every production build is inspected for baseline security controls before deployment.
Findings at this stage are deterministic and easy to remediate. They reduce noise during later testing phases and prevent recurring configuration mistakes from reaching production.
This approach also supports compliance and audit requirements. Organizations aligning with standards such as ISO 27001 compliance benefit from consistent evidence of secure build practices and continuous validation.
For broader coverage, IPA assessment can be integrated alongside other application security services and advanced testing platforms such as SLASH to create a layered security strategy.
| Issue Found in IPA | Why It Happens | How It Appears in IPA | Security Impact |
|---|---|---|---|
| ATS disabled or weakened | Legacy backend compatibility or temporary testing changes | Relaxed App Transport Security rules | MITM and traffic interception |
| Hardcoded API keys | Build-time injection or third-party SDK defaults | Keys embedded in app bundle resources | Unauthorized service access |
| Embedded OAuth tokens | CI/CD misconfiguration or test credentials | Access tokens present in binary or assets | Account takeover and abuse |
| Excessive entitlements | Template inheritance or copied provisioning profiles | Broad capability grants beyond app scope | Privilege escalation post-compromise |
| Debug flags enabled | Release build misconfigured as debug | Debug options and logging resources present | Sensitive information disclosure |
| Weak binary hardening | Compiler flags changed or misapplied | Missing PIE, stack canaries, encryption | Reduced exploit resistance |
| Unsafe URL schemes | Convenience features without threat modeling | Custom schemes exposed without validation | Intent hijacking and data leakage |
| Unused permissions declared | Over-scoped capability requests | Privacy usage strings without functional need | Unnecessary privacy exposure |
When Manual Reverse Engineering Is Still Required
While IPA vulnerability assessment is highly effective for identifying build-time and configuration issues, it does not replace all forms of iOS security testing.
Manual reverse engineering remains essential for analyzing complex authorization logic, custom cryptographic implementations, obfuscation mechanisms, and anti-debugging techniques. These scenarios require runtime context and human reasoning.
The key difference is prioritization. By eliminating low-signal work early, IPA assessment allows manual testing to focus on high-impact attack surfaces rather than baseline hygiene.
IPA vulnerability assessment is not a shortcut around iOS security testing. It is a pragmatic response to how modern iOS applications are built and deployed.
By validating OWASP MASVS controls directly against the IPA file, security teams can identify common and impactful vulnerabilities faster, earlier, and more consistently than with manual testing alone. Tools such as the IPA Security Analyzer make this process repeatable and scalable, without replacing the need for deeper analysis where it truly matters.
In modern iOS AppSec programs, treating the IPA as a first-class security artifact is no longer optional. It is the foundation on which effective, sustainable mobile security testing is built.




